Fortinet Acquires Next DLP Strengthens its Top-Tier Unified SASE Solution
Read the release

In an era where data breaches and insider threats loom large over corporations, understanding the landscape of data exfiltration vectors has never been more crucial. In January 2024, we analyzed data from the Reveal Platform to better understand the mechanisms through which sensitive data is leaked out of corporate networks. Leveraging the analytics of our insider risk and data loss prevention software platform, we embarked on a comprehensive study to unearth the patterns and prevalence of data exfiltration across hundreds of organizations.
This research was not merely an academic exercise but a practical foray into the frontlines of cybersecurity defense. By analyzing real-world interactions with our platform, we aimed to identify the most commonly leveraged exfiltration vectors by insiders—whether through negligence or malice. Our findings offer a unique vantage point into the dynamics of data security in the modern enterprise, providing invaluable insights into the tools and tactics employed by individuals to navigate around established security measures.
Armed with this knowledge, the following post delves into the specifics of these exfiltration vectors, shedding light on their intricacies and the implications for organizations striving to safeguard their digital assets. From the subtle misuse of seemingly benign applications to the outright theft of data via sophisticated techniques, our analysis paints a comprehensive picture of the current threat landscape. By aligning our observations with the MITRE ATT&CK framework, we offer cybersecurity professionals a roadmap to not only recognize these threats but to effectively counteract them, fortifying their defenses against the ever-evolving tactics of data exfiltrators.
We know from MITRE’s Insider Threat research that:
Our researchers investigated exfiltration detections across hundreds of companies during January 2024. We define detection as a suspicious activity occurring on an endpoint or in a cloud app that:
For example, a policy detection indicates when a user attempts to copy a sensitive file to a USB storage device. A behavioral analytics detection indicates when a user copies a sensitive file to a USB storage device when they normally do not use such devices, or does so outside of normal business hours.
Using MITRE’s terminology, a detection can be thought of as an observed human indicator (OHI) that details the tactics, techniques and procedures (TTPs) that insiders use on information systems.
|
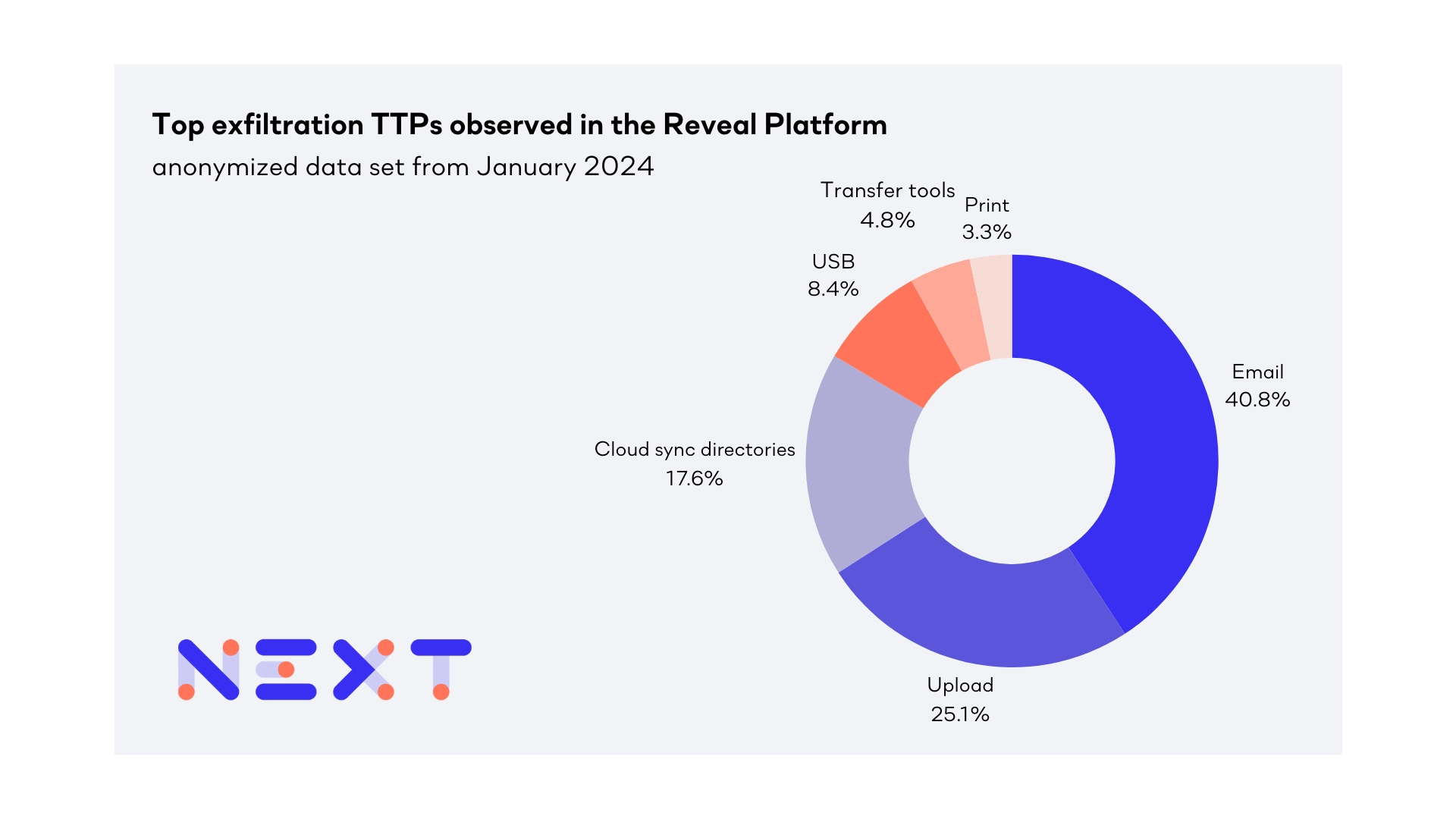
Ordered from the most frequent to the least frequent, the observed exfiltration techniques in the Reveal Platform are:
Here’s a deep dive into what our researchers found about each TTP.
Sub-techniques: T1114.001 - Local email collection
Email is the most prevalent vector for data exfiltration, no suppose considering its simplicity and popularity. 40.8% of the exfiltration detections were triggered by an action in an email application. We detected insiders using email to collect and exfiltrate sensitive information. Email’s ease of use and universal access make it a convenient channel for sending and receiving information, including sensitive data, thereby increasing the risk of unintended disclosure or malicious exfiltration. Emails may contain sensitive data, including trade secrets or personal information. Emails often hold critical information, including proprietary business secrets or individual personal details, which can be of significant value in the outside world.
Upload - MITRE ATT&CK ID: T1567
Sub-techiques:
T1567.001 - Exfiltration to code respository
T1567.002 - Exfiltration to cloud storage
T1567.003 - Exfiltration to text storage sites
What we mean by Upload is the uploading of data via a browser.
A browser upload is a common method for insiders to leak data from their employers for several reasons, many of which are tied to the accessibility and ease of use of web technologies, as well as the challenges organizations face in monitoring and controlling data movement.
25.1% of the exfiltration detections were triggered by insiders uploading sensitive data to cloud apps and storage using their browser. A malicious employee may know that organizations have controls to monitor email traffic and file transfers over the network, but distinguishing between legitimate and malicious browser uploads can be challenging for their employer. Text storage sites, such as pastebin, are commonly used by developers to share code and other information. Personal logins, paid features and encryption options may make it easier for malicious insiders to conceal and store data.
Exfiltration Over Web Service: Exfiltration to Cloud Storage
What we mean by cloud sync directory is an agent on an endpoint that syncs local folder(s) to the cloud e.g. Dropbox or iCloud. It's no surprise that the most frequent exfiltration technique we see in Reveal aligns with MITRE’s Impact Report findings.
17.6% of the exfiltration detections were from insiders transferring data to personal online storage services and accounts instead of using a company approved account or storage service. Online storage services enable data to be stored, modified, and retrieved from a remote endpoint via the Internet. It’s worth mentioning that, due to sync agent misconfiguration, users may be synching data without even realizing it. Transferring data to these services can offer considerable concealment for a malicious insider, especially if other corporate devices are already interacting with these services.
Exfiltration Over Physical Medium: Exfiltration over USB
We detected insiders attempting to exfiltrate data over a USB connected physical device. The small, lightweight, and easy to conceal nature of USB devices makes them highly portable and convenient for transporting large amounts of data. An employee can quickly download a significant volume of information onto a USB drive and physically remove it from the premises without attracting attention.
8.4% of the exfiltration detections were triggered by an employee transferring data to a USB device. Under specific conditions, like the breach of an air-gapped network, data could be siphoned off through a USB device brought in by a user. This USB device might serve as the ultimate point of data leakage or act as a bridge to transfer data across systems that are not connected to each other.
Sub-techniques:
T1048.001 - Exfiltration over symmetric encrypted non-C2 protocol
T1048.002 - Exfiltration over asymmetric encrypted non-C2 protocol
T1048.003 - Exfiltration over unencrypted non-C2 protocol
Despite its utility for legitimate purposes, the characteristics such as automation, anonymity, encryption, and bypassing security measures, that make transfer tools like ftp convenient and powerful also make it a potential tool for malicious insiders. 4.8% of the exfiltration detections were from the use of transfer tools, moving company data to alternate network locations using a managed endpoint. This exfiltration technique can be done using various common operating system utilities such as ftp, sftp, scp and rsync. Malicious insiders sometimes encrypt and/or obfuscate these alternate channels.
Exploiting printers as a weak link in the security chain is a technique used by malicious insiders. 3.3% of the exfiltration detections were triggered by printer activity. The most straightforward method involves printing confidential or sensitive documents and physically removing them from the premises. Home printers can also be an exfiltration vector for sensitive information in various scenarios, particularly with the rise of remote work and the increasing integration of smart technology into home office environments. Malicious insiders also use capabilities in modern printers to fax or email documents directly from the printer itself.
In conclusion, the insights from the Reveal Platform by Next DLP in January 2024 underline a critical challenge facing organizations today: shadow SaaS and the diverse tactics insiders use to cause data leaks. As we have seen, the utilization of unauthorized SaaS applications can significantly amplify the risks of data exposure, undermining the security, compliance, and data integrity of organizations. From the most common method of email exfiltration to the more nuanced use of cloud sync directories, USB devices, transfer tools, and even printers, the range of exfiltration techniques reflects both the creativity of insiders and the vulnerabilities in current corporate defenses.
The alignment of these exfiltration vectors with the MITRE ATT&CK framework not only provides a structured understanding of the threat landscape but also equips cybersecurity professionals with the knowledge to anticipate and mitigate these risks effectively. The prevalence of email as an exfiltration vector, for example, underscores the need for robust monitoring and control mechanisms for both traditional and web-based email applications. Similarly, the significant percentages of data exfiltration through uploads, cloud sync, and physical media like USB devices highlight the urgent need for comprehensive endpoint and network security solutions that can detect and prevent unauthorized data movement.
To safeguard against these threats, organizations must adopt a proactive stance, incorporating advanced detection technologies, employee education, and a culture of security awareness. It is also essential for security teams to understand the behavioral and technical nuances of data exfiltration techniques to develop more effective countermeasures.
As the digital landscape evolves and the adoption of SaaS applications continues to grow, our findings from the Reveal platform serve as a crucial reminder of the ongoing battle against data exfiltration. By staying informed and vigilant, organizations can better protect their most valuable assets in an increasingly interconnected and precarious cyber environment.

Blog

Blog

Blog

Blog

Resources

Resources

Resources

Resources
